
Nearly all criminals have a common modus operandi: go for the biggest paycheck for the least effort. They also prefer a sure thing over risk and familiar ground over having to learn new skills.
Linux, while generally considered a relatively secure operating system, has become today's low-hanging fruit due to its popularity in embedded IoT devices.
Next Gen Botnets - More Problematic
Further, Distributed Denial of Service (DDoS) has become a popular tool for attackers. With DDoS, attackers conscript a diverse, distributed army of IoT devices to launch massive attacks.
A Perfect Storm
Botnets, also called a zombie army are a set of Internet connected computers infected with malware - unknown to the user and controlled by cybercriminals. While botnets are not new, IoT-based botnets represent a new threat to cybersecurity.
A number of factors have come into alignment for IoT-based botnets over the past few years:
- Linux malware, along with source code, has become readily available on the Internet
- Aging, vulnerable Linux devices have been on the Internet for nearly two decades
- Hackers have developed effective strategies to automate the process of finding, infecting and controlling vulnerable targets
- DDoS attacks are thriving and are very economical for attackers
These are some of the reasons why DDoS attacks have increased in both strength and volume this year.
The result is that almost anyone can enlist millions of Linux-based IoT devices to achieve 'hacktivism,' be it against government agencies, news organizations, major corporations or even freelance journalists.
And until the security industry comes up with better mitigation strategies, things are going to get a lot worse before they get better.
Case Study: KrebsOnSecurity - Mirai Botnet Attack
The website of cybersecurity journalist Brian Krebs - KrebsOnSecurity.com - was taken down in September 2016 by what was one of the largest DDoS attacks to date. The source code for this attack - dubbed 'Mirai' - was later released in October on the hacking community website Hackforums.
A story by Krebs named two individuals in the illegal DDoS-for-hire service - vDOS - and may have subsequently led to their arrests.
The unknown perpetrators that launched the KrebsOnSecurity attack allegedly did so in retaliation for Krebs’ story.
The attack on Krebs' website was unique for a number of reasons.
At 620Gbps, it was one of the largest DDoS attacks in the history of the Internet. The botnet encompassed hundreds of thousands of embedded Linux devices, including Small Office/Home Office (SOHO) routers, DVRs, surveillance cameras and other IoT devices.
Particularly remarkable in this case is that the attack traffic came directly from botnet devices to Krebs' website. In contrast, DDoS attacks are usually redirected through common internet services like DNS to amplify attacks and/or hide the identity of botnet nodes.
Next-Gen Botnets More Dangerous
Several factors make IoT-based botnets more dangerous than botnets in the past.
Botnets in the past typically consisted of compromised Windows PCs, which IT could usually ‘blacklist’ without much impact to businesses.
In contrast, the KrebsOnSecurity botnet included devices that provide internet connectivity. In such cases, security professionals can’t 'blacklist' the devices without blocking countless consumers from large portions of the Internet.
Another problem is the economics of DDoS attacks: launching a DDoS attack can cost as little as $5.
This cost imbalance obviously tips the scale in favor of attackers, and only the largest enterprises can afford sufficient protection.
IoT Security Concerns
In a recent 451 Alliance IoT study, respondents who cited security concerns when it comes to IoT initiatives were asked about their greatest worries -
Physically Unsecure Endpoints (63%) and
Poor Authentication of IoT Endpoints (55%) topped the list.
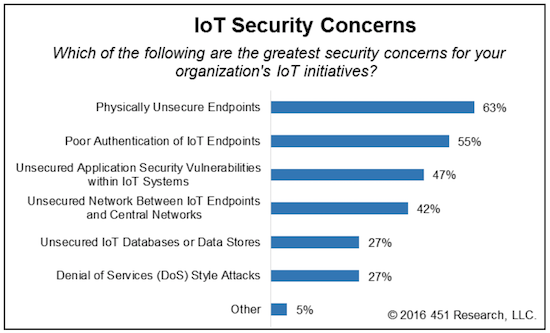
Other major security issues include the
Unsecured Application Security Vulnerabilities within IoT Systems (47%) and
Unsecured Network Between IoT Endpoints and Central Networks (42%).
High-Speed Attacks
Another recent attack against OVH (an ISP) exceeded 1Tbps, making it the largest DDoS attack ever (although only about 150,000 devices were involved in the attack).
To illustrate just how massive a 1Tbps attack is, imagine 150,000 people trying to simultaneously binge-watch Netflix over a single Wi-Fi connection.
Outlook: The Good, the Bad, and the Ugly
The Good: Recent attacks could represent an inflection point for IoT security, causing device manufacturers to build products with native security capabilities.
If device manufacturers do begin to pay greater attention to IoT security, it could spur increased funding into security startups.
In addition, large IT security vendors could accelerate product development to deal with IoT security concerns.
The Bad: Given the success of recent attacks, it is unlikely that they will slow down, even if vendors pay greater attention to security.
The ease with which these attacks are launched, and the difficulty of protecting against them, will further incentivize attackers.
In addition, the scale of attacks will increase dramatically as IoT grows and more devices are connected.
The Ugly: The time frame for replacing IoT devices is especially long. If a camera, DVR, router or other device works, users aren't likely to replace them.
Since many of these devices are old by IT standards, and were built without security in mind, many of them lack the capability for Over-the-Air (OTA) software updates. As such, these vulnerable devices can't be patched easily.
The Really Ugly: Whenever attacks exceed 300Gbps, radiating effects can ripple into adjacent networks and users. Now that some attacks exceed 1Tbps capacity, they are surpassing the speeds of some carrier-grade network equipment.
Soon, attackers will have the ability to take down large network segments, not just a website here or there.

To receive more articles like this, join the
451 Global Digital Infrastructure Alliance. The 451 Alliance is a member-driven 'think tank' comprised of a worldwide network of highly-qualified enterprise technology and IT professionals. The 451 Alliance tracks changes in corporate IT and digital infrastructure technologies well in advance of other sources and reports findings directly to its members.
Thanks to our partnership we are able to offer our members a complimentary membership to the 451 Alliance. Membership includes access to 451 Alliance’s weekly research reports and a bi-weekly newsletters.
Join now!
Opinions expressed by the author are not necessarily those of WITI.
Are you interested in boosting your career, personal development, networking, and giving back? If so, WITI is the place for you! Become a WITI Member and receive exclusive access to attend our WITI members-only events, webinars, online coaching circles, find mentorship opportunities (become a mentor; find a mentor), and more!
Founded in 1989, WITI (Women in Technology International) is committed to empowering innovators, inspiring future generations and building inclusive cultures, worldwide. WITI is redefining the way women and men collaborate to drive innovation and business growth and is helping corporate partners create and foster gender inclusive cultures. A leading authority of women in technology and business, WITI has been advocating and recognizing women's contributions in the industry for more than 30 years.
The organization delivers leading edge programs and platforms for individuals and companies -- designed to empower professionals, boost competitiveness and cultivate partnerships, globally. WITI’s ecosystem includes more than a million professionals, 60 networks and 300 partners, worldwide.
WITI's Mission
Empower Innovators.
Inspire Future Generations.
Build Inclusive Cultures.
As Part of That Mission WITI Is Committed to
Building Your Network.
Building Your Brand.
Advancing Your Career.

 Nearly all criminals have a common modus operandi: go for the biggest paycheck for the least effort. They also prefer a sure thing over risk and familiar ground over having to learn new skills.
Nearly all criminals have a common modus operandi: go for the biggest paycheck for the least effort. They also prefer a sure thing over risk and familiar ground over having to learn new skills. 

Comments